Utilizziamo i cookie per rendere migliore la tua esperienza di navigazione. Per rispettare la nuova direttiva sulla privacy, è necessario chiedere il tuo consenso per impostare i cookie. Per saperne di più.
The digital signature suite emSecure, is a SEGGER software package that allows creation and verification of digital signatures. One important feature is that emSecure can make it impossible to create a clone of an embedded device by simply copying hardware and firmware. And it can do much more, such as securing firmware updates distributed to embedded devices and authenticating licenses, serial numbers, and sensitive data.
emSecure offers 100% protection against hacking. It is not just nice to have, but in fact a must-have, not only for critical devices such as election machines, financial applications, or sensors. Compromised devices are dangerous in several ways, not just from a commercial point of view. They hamper manufacturers' reputation and might entail severe legal disputes. Not addressing the issue of hacking and cloning is irresponsible. Based on asymmetric encryption algorithms with two keys, emSecure signatures cannot be forged by reverse engineering of the firmware.
A secure private key is used to generate the digital signature, whereas a second, public key is used to authenticate data by its signature. There is neither a way to get the private key from the public key, nor is it possible to generate a valid signature without the private key.
The emSecure source code has been created from scratch for embedded systems, to achieve highest portability with a small memory footprint and high performance. However, usage is not restricted to embedded systems. With its easy usage, it takes less than one day to add and integrate emSecure into an existing product.
emSecure is a very complete package, including ready-to-run tools and functionality for generation of keys and signatures for your embedded solution.
emSecure has been created from scratch to achieve highest portability and performance with a very small memory footprint. It enables you to profit from the security of digital signatures in embedded applications, even on small single-chip microcontrollers without the need of additional hardware such as external security devices or external memory.
SEGGER offers different versions of emSecure which use different signature algorithms to fit any requirement of size or speed. The structure of each version is similar to make all of them easily usable and expandable.
emSecure is a complete package. It includes ready-to-run tools to generate keys and signatures, to sign and verify data and to convert the keys and signatures into compilable formats. emSecure includes all required source code to integrate signature generation directly into your production process and data verification into your application or firmware.
emSecure has a simple yet powerful API. It can be easily integrated into an existing application within one day. emSecure incorporates proven security algorithms as proposed by NIST. The algorithms are proven to be cryptographically strong and can provide a maximum of security to your applications.
emSecure is licensed in the same way as other SEGGER middleware products and not covered by an open-source or required-attribution license. It can be integrated in any commercial or proprietary product without the obligation to disclose the combined source. It can be used royalty-free in your product.
emSecure includes a sample application project, which demonstrates the verification of a signed message.
The sample application project is available for evaluation upon request. Contact us at info@segger.com.
Sample Project
The sample project is a SEGGER Embedded Studio solution. It can be run in the SEGGER Embedded Studio Simulator as well as on real Cortex-M3 / Cortex-M4 hardware.
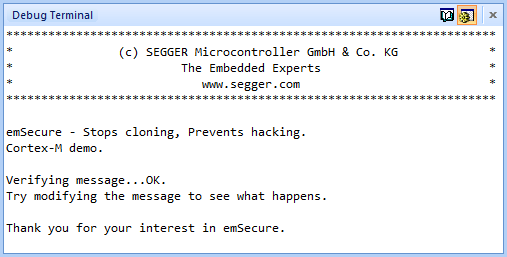
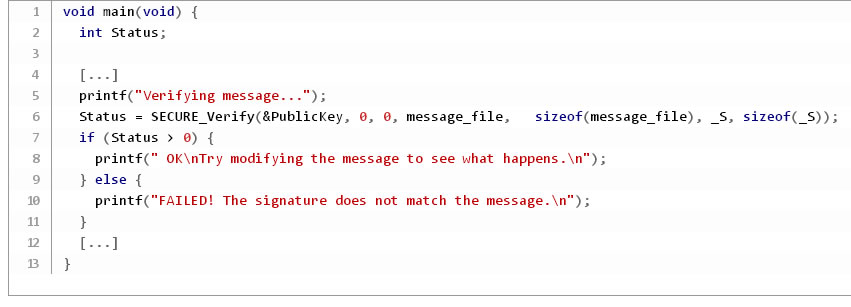
The application is simple. The sample includes a Message.txt, which can be signed with emSign and the included sample keys. Message and signature are converted into compilable buffers and can be included in the application. The application runs the verification on the message with the signature, which will only pass when neither the message nor the signature are modified. The message can be changed, signed and converted with the included tools.
emSecure is available in different versions which use different signature algorithms. Each signature algorithm has different characteristics. The emSecure products can provide security for any requirement of size or speed. The table below lists some benefits of the different emSecure versions. For a complete overview and performance values, please refer to the subpage of the product.
| emSecure version | Pro |
|---|---|
| emSecure-RSA |
|
| emSecure-ECDSA |
|
The Sign & Verify Application enables easy drag-and-drop creation of emSecure digital signatures and verification of signed files. It may be used freely for personal use too, for example make sure files stored on a server are not changed or to allow communication partners to send/receive files knowing nothing has been changed during transmission. More information about emSecure Sign & Verify.
emSecure is a complete package that comes with everything needed: A utility to generate the private and public keys, code to calculate secure hashes, encrypt, decrypt messages as well as create and verify digital signatures.
All parts of the package conform to the relevant FIPS specifications issued by NIST and have been tested against standard test vectors, to prove the implementation.
emSecure is provided in source code with example applications precompiled for your convenience.
The source code gives complete control of the code that goes into a product and its production facility.
When it comes to the degree of security emSecure offers an easy answer: It is unbreakable because no one can generate a valid signature without knowledge of the private key.
Putting enough effort into getting the bootloader or firmware image, disassembling, analyzing it, and modifying the application to bypass the security measures, hackers might be able to clone a product or use alternative firmware images. However this will only work until a firmware update is done.
There are additional ways to increase overall system security:
- • The private key has to be kept private.
- • Private keys should best be generated on a dedicated machine that has no connection to a network and controlled access.
- • RSA private keys can be generated from a pass-phrase, which means the pass-phrase should not be too easy to guess.
- • The pass-phrase length is not limited.
- • The company name is not a good choice.
- • The pass-phrase has to be kept private, too.
- • The private key might also be encrypted and is only decrypted while it is used in production.
- • The bootloader should be stored in a memory which can be protected against read- and write-access.
- • The firmware should be protected against external read-access.
- • The verification process can be done in multiple places of the application. A tool communicating with the product, like a PC application, might carry our additional checks.
I WANT TO INHIBIT COPYING A WHOLE FIRMWARE FROM ONE PRODUCT HARDWARE TO ANOTHER CLONED ONE. HOW CAN I PREVENT IT TO BE RUN FROM THE CLONED VERSION WITH EMSECURE?
A: Nearly every modern MCU includes a unique ID which is different on every device. When the signature covers this UID it is only valid on one single device and cannot be run on a cloned or copied product. The firmware can verify the signature at boot-time.
I ADDED A DIGITAL SIGNATURE TO MY PRODUCT. WHERE SHOULD I VERIFY IT?
A: Signature verification can be done in-product or off-product. With in-product verification the firmware for example verifies the digital signature at boot-time and refuses to run when the signature cannot be verified. With off-product verification an external application, e.g. a PC application communicating with the device, reads the signature and data from the product in order to verify it.
I WANT MY PRODUCT TO ONLY RUN GENUINE FIRMWARE IMAGES. HOW CAN I ACHIEVE THIS WITH EMSECURE?
A: To make sure a firmware image is genuine, the complete image can be signed with a digital signature. For instance while using a CRC for integrity checks, the signature is sent with the firmware data upon a firmware update. The application or bootloader programming the firmware onto the device, validates the firmware data with its signature. The signature can only be generated with the private key and should be provided by the developer through the firmware data.
I AM PROVIDING ADDITIONAL LICENSES FOR MY PRODUCT WHICH SHALL BE LOCKED TO A SPECIFIC USER OR COMPUTER. CAN I GENERATE LICENSE KEYS WITH EMSECURE?
A: Yes. emSecure can generate unique license keys for any data, like a computer ID, a user name, e-mail address, or any other data.
MY PRODUCT IS SENDING DATA TO A COMPUTER APPLICATION. CAN I MAKE SURE THE COMPUTER APPLICATION IS GETTING DATA ONLY FROM MY PRODUCT WITH EMSECURE?
A: Yes. In this case the product is used to sign the data and the computer application verifies it. To prevent the private key from being read from the product, it might be stored encrypted on the product or in the application and decrypted prior to signing the data.
DOES EMSECURE SUPPORT DSA?
A: No, but signing and verification code are available from SEGGER. Please get in touch with us if you feel DSA signature verification is what you need.
MY QUESTION IS NOT LISTED ABOVE. WHERE CAN I GET MORE INFORMATION?
A: For more information feel free to contact us at info@segger.com
- Asymmetric algorithms - Dual keys, private, and public make it 100% safe
- Different algorithms available - Fitting any requirements
- Hardware-independent, any CPU and no additional hardware needed
- High performance, small memory footprint
- Simple API, easy to integrate
- Applicable for new and existing products
- Complete package, key generator, and tools included
- Full source code available
- Free 'Sign & Verify' Windows Version to Protect Personal Files
Non esitare a metterti in contatto con i nostri esperti.
Basta chiedere qui



